Free 2014 Cisco 200-101 Dump (41-50) Download!
QUESTION 41
Which two statements describe the process identifier that is used in the command to configure OSPF on a router? (Choose two.)
Router(config)# router ospf 1
A. All OSPF routers in an area must have the same process ID.
B. Only one process number can be used on the same router.
C. Different process identifiers can be used to run multiple OSPF processes
D. The process number can be any number from 1 to 65,535.
E. Hello packets are sent to each neighbor to determine the processor identifier.
Answer: CD
Explanation:
we all know that The areas can be any number from 0 to 4.2 billion and 1 to 65,535 for the Process ID.
The process ID is the ID of the OSPF process to which the interface belongs. The process ID is local to the router, and two OSPF neighboring routers can have different OSPF process IDs. (This is not true of Enhanced Interior Gateway Routing Protocol [EIGRP], in which the routers need to be in the same autonomous system). Cisco IOS Software can run multiple OSPF processes on the same router, and the process ID merely distinguishes one process from the another. The process ID should be a positive integer.
QUESTION 42
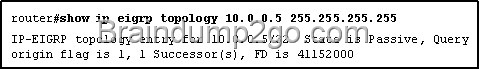
Refer to the exhibit. Given the output from the show ip eigrp topology command, which router is the feasible successor?
Answer: B
QUESTION 43
Which three of these statements regarding 802.1Q trunking are correct? (Choose three.)
A. 802.1Q native VLAN frames are untagged by default.
B. 802.1Q trunking ports can also be secure ports.
C. 802.1Q trunks can use 10 Mb/s Ethernet interfaces.
D. 802.1Q trunks require full-duplex, point-to-point connectivity.
E. 802.1Q trunks should have native VLANs that are the same at both ends.
Answer: ACE
Explanation:
To be the feasible successor, the Advertised Distance (AD) of that route must be less than the Feasible Distance (FD) of the successor. From the output of the “show ip eigrp topology 10.0.0.5 255.255.255.255 we learn that the FD of the successor is 41152000. Now we will mention about the answers, in the “Composite metric is (…/…)” statement the first parameter is the FD while the second parameter is the AD of that route. So we need to find out which route has the second parameter (AD) less than 41152000 -> only answer B satisfies this requirement with an AD of 128256.
QUESTION 44
Which two options are valid WAN connectivity methods? (Choose two.)
A. PPP
B. WAP
C. DSL
D. L2TPv3
E. Ethernet
Answer: AC
Explanation:
Explanation:
On each WAN connection, data is encapsulated into frames before itcrosses the WAN link. The following are typical WAN protocols:1. High-level Data Link Control (HDLC): The Cisco default encapsulation type onpoint-to-point connections, dedicated links, and circuit- switches connections.2. PPP: Provides router-to-router and host-to-network connections over synchronous andasynchronous circuits. PPP was designed to work with several network layer protocols,including IP.3. Frame-relay: A successor to X.25. This protocol is an industry-standard, switchesdata-link layer protocol that handles multiple virtual circuits
http://en.wikipedia.org/wiki/Wide_area_network
http://www.ciscopress.com/articles/article.asp?p=102157&seqNum=2
QUESTION 45
What occurs on a Frame Relay network when the CIR is exceeded?
A. All TCP traffic is marked discard eligible.
B. All UDP traffic is marked discard eligible and a BECN is sent.
C. All TCP traffic is marked discard eligible and a BECN is sent.
D. All traffic exceeding the CIR is marked discard eligible.
Answer: D
Explanation:
Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the Frame Relay switch. Frames that are sent in excess of the CIR are marked as discard eligible (DE) which means they can be dropped if the congestion occurs within the Frame Relay network.
Note: In the Frame Relay frame format, there is a bit called Discard eligible (DE) bit that is used to identify frames that are first to be dropped when the CIR is exceeded.
QUESTION 46
What are two characteristics of Frame Relay point-to-point subinterfaces? (Choose two.)
A. They create split-horizon issues.
B. They require a unique subnet within a routing domain.
C. They emulate leased lines.
D. They are ideal for full-mesh topologies.
E. They require the use of NBMA options when using OSPF.
Answer: BC
Explanation:
http://www.ciscopress.com/articles/article.asp?p=170741&seqNum=5
QUESTION 47
Which two statements about using the CHAP authentication mechanism in a PPP link are true? (Choose two.)
A. CHAP uses a two-way handshake.
B. CHAP uses a three-way handshake.
C. CHAP authentication periodically occurs after link establishment.
D. CHAP authentication passwords are sent in plaintext.
E. CHAP authentication is performed only upon link establishment.
F. CHAP has no protection from playback attacks.
Answer: BC
Explanation:
http://www.cisco.com/en/US/tech/tk713/tk507/technologies_tech_note09186a00800b4131.shtml
QUESTION 48
Which command allows you to verify the encapsulation type (CISCO or IETF) for a Frame Relay link?
A. show frame-relay lmi
B. show frame-relay map
C. show frame-relay pvc
D. show interfaces serial
Answer: B
Explanation:
map will show frame relay encapsulation (cisco or ietf) http://www.cisco.com/en/US/docs/ios/12_2/wan/command/reference/wrffr4.html#wp1029343
QUESTION 49
What is the purpose of Inverse ARP?
A. to map a known IP address to a MAC address
B. to map a known DLCI to a MAC address
C. to map a known MAC address to an IP address
D. to map a known DLCI to an IP address
E. to map a known IP address to a SPID
F. to map a known SPID to a MAC address
Answer: D
Explanation:
Frame-Relay (a Layer 2 protocol) uses Inverse-Arp to map a know Layer 2 Address (DLCI) to a unknow Layer 3 Address.
QUESTION 50
What information does a router running a link-state protocol use to build and maintain its topological database? (Choose two.)
A. hello packets
B. SAP messages sent by other routers
C. LSAs from other routers
D. beacons received on point-to-point links
E. routing tables received from other link-state routers
F. TTL packets from designated routers
Answer: AC
Explanation:
http://www.cisco.com/en/US/tech/tk365/technologies_white_paper09186a0080094e9e.shtml
If you want to pass the Cisco 200-101 Exam sucessfully, recommend to read latest Cisco 200-101 Dumpfull version.
![clip_image001[13] clip_image001[13]](http://examgod.com/l2pimages/Free2014Cisco200101Dump4150Download_9D87/clip_image00113_thumb.jpg)
![clip_image001[15] clip_image001[15]](http://examgod.com/l2pimages/Free2014Cisco200101Dump4150Download_9D87/clip_image00115_thumb.jpg)
![clip_image001[17] clip_image001[17]](http://examgod.com/l2pimages/Free2014Cisco200101Dump4150Download_9D87/clip_image00117_thumb.jpg)
![clip_image001[19] clip_image001[19]](http://examgod.com/l2pimages/Free2014Cisco200101Dump4150Download_9D87/clip_image00119_thumb.jpg)
